US State Dept has no idea if its IT security actually works, say auditors
End-of-life systems still in use, poor inventory control, and China's hunting
Updated The US Department of State has largely failed to implement an effective cybersecurity risk program, auditors concluded in a report last week. That means a crucial arm of the American government is potentially wide open to cyberattacks it may not be able to identify or stop.
The State Department, which handles diplomacy and US foreign policy, wrote a risk management strategy for its IT security, the Government Accountability Office (GAO) said, and that's basically where the dept gave up. As a result, department-wide risks haven't actually necessarily been mitigated, there's no overall monitoring program in place, and IT infrastructure used by the department may not have been adequately secured.
"Until the department implements required risk management activities, it lacks the assurance that its security controls are operating as intended," the GAO said in its report. "Moreover, State is likely not fully aware of information security vulnerabilities and threats affecting future operations."

Still a bit of work to be done on implementing that risk management program ... Auditors' findings after looking into the State Dept's progress ... Click to enlarge
The State Department was among the federal government agencies that had data stolen by suspected Chinese snoops when the spies managed to gain access to Microsoft-hosted email services used by Uncle Sam. Some 60,000 unclassified messages belonging to State officials were swiped by the intruders, the department said.
"The department takes seriously its responsibility to safeguard its information and continuously takes steps to ensure information is protected," a State Department spokesperson told The Register. "Like every large organization with a global presence, we closely monitor cybersecurity conditions."
While it's unlikely better cybersecurity habits at the State Department could have directly prevented that email theft via Microsoft accounts, due to blunders by the Azure giant itself, the issue serves to illustrate the seemingly poor state of US government cybersecurity. The GAO has called attention to this before, saying in January that nearly 60 percent of the security recommendations it has made since 2010 have yet to be implemented.
And implement the State Department must, because things are potentially really bad over there. "Certain installations of operating system software had reached end-of-life over 13 years ago" bad, in fact.
Along with its vintage OSes, State is operating 23,689 systems and 3,102 "network and server operating system software installations" that have reached end of life. With so many outdated systems on its networks, State's IT infrastructure is highly susceptible to known exploits and may be "unable to fully detect, investigate and mitigate cybersecurity-related incidents," the GAO warned.
A federated mess
A good portion of the blame for the State Department's cybersecurity planning failures falls, at least according to the GAO, on State's federated structure that splits IT management responsibilities between the department's CIO and also other sub-organizations.
That way of doing business "limits the CIO's ability to effectively oversee the department's IT security posture," the GAO said, which is only made worse by an "insulated culture" (eg, State's various bureaus operate largely independently) that has led to communication issues.
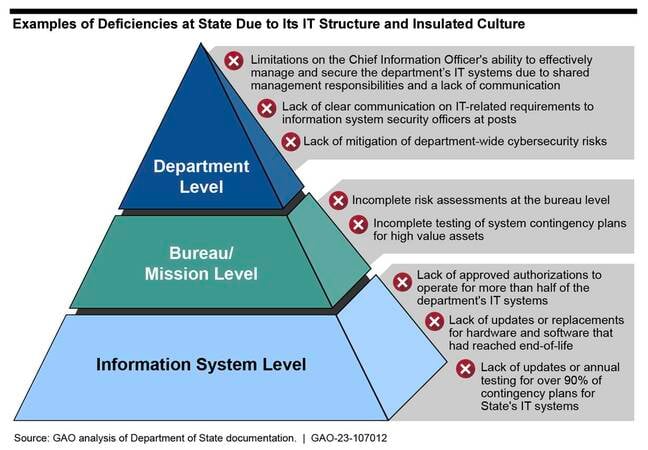
Deficiencies in State Dept security due to its insulated culture, according to GAO ... Click to enlarge
As one example, the GAO said the State Department's enterprise configuration management (ECM) database – used to track IT assets and inventory being used by the dept – is missing details of various bits of hardware and software in use because it's limited to documenting stuff specific to just one operating system. Further, the ECM database wasn't configured to capture data from 20 diplomatic outposts, meaning all of their network assets are absent. The department also isn't capturing network data that crosses its firewalls, GAO found.
The communication breakdown at the State Department also means that contrary to its risk management framework, which specifies that the CIO must grant or deny requests to deploy and operate systems, around 56 percent of such systems were running without proper authorization, 15 high-value assets and seven high-risk systems among them.
Carry on breaching
The GAO's conclusions are stark. If these issues aren't fixed it'll be potentially open season on one of the most important agencies in the American government.
"Securing the information and systems that support State's mission is crucial to the department's ability to effectively manage its cybersecurity risks," the GAO stated, noting that the progress made in recent years hasn't been enough to get the State Department into shape.
- US State Department opens cybersecurity policy bureau
- US government to investigate China's Microsoft email breach
- The Pentagon has no idea how to deal with bad cloud contracts, say auditors
- NSA hopes AI Security Center will help US outsmart, outwit, and outlast adversaries
Because it hasn't implemented a continuous monitoring strategy, State won't be able to fully understand its risk posture; likewise, because it hasn't implemented an incident response process and uses outdated systems, State is unable to effectively detect and respond to vulnerabilities "before they become incidents."
The GAO made 15 recommendations to the State Department which, as you may expect, have to do with implementing various elements of its planned cyber risk management strategy that have sat idle since development.
But that's not all - because of the sensitive nature of many of the findings, the GAO said it will release a limited-distribution report focusing on "technical security control deficiencies in State's IT infrastructure" later on. That report, the GAO said, will detail 40 deficiencies identified across three State Department bureaus and 16 posts, and includes "about 500" recommendations. In other words, pity the poor IT staff who support those diplomats. ®
Updated at 1412 UTC on October 3, 2023, to add
A State Department spokesperson sent us an additional statement:
"The GAO began this review in 2019 and the report represents a snapshot in time. The State Department values the insight and accountability that the GAO provides. The Department is prioritizing and addressing those recommendations that remain current and coordinating with the GAO to resolve those that the Department has already addressed.
"Since 2019, the State Department has made meaningful improvements in operational cybersecurity and cybersecurity governance, to include significantly increasing multi-factor authentication and data encryption and standing-up the Department Chief Information Security Office in 2021. The office has driven rapid improvements through the introduction of cybersecurity oversight and a shared responsibility model, including bureau-level cybersecurity scorecards."
 Biting the hand that feeds IT
Biting the hand that feeds IT